eCPPTv3 review
I recently completed the eCPPTv3 exam—and honestly, I don’t recommend it.
While the environment was stable and the tools worked fine, the exam content was disappointing. For a certification that markets itself as “professional,” it falls short in multiple areas that matter.
My Background
By the time I took the eCPPTv3, I had a solid foundation in penetration testing—particularly in Active Directory attacks. I completed the CRTP certification over three years ago, regularly solve machines on Hack The Box (HTB), and have spent a lot of time building my own custom AD labs. I chose eCPPTv3 because it was offered at a discounted price. I thought it could be a good opportunity to reinforce my skills or learn something new. While the lab environment was stable and the tools worked fine, the exam content left much to be desired.
The Course
The course tries to cover a wide range of topics including Windows and Linux privilege escalation, web exploitation, and some Active Directory techniques. While it gives a decent introduction to these areas, it lacks depth across the board. The AD section barely scratches the surface, and without prior experience, it’s easy to miss the bigger picture. The web exploitation content mostly focuses on attacking CMS platforms and doesn’t cover much beyond that. The material isn’t very exam focused either-many of the techniques used during the assessment aren’t explained well or at all in the course. If you’re already experienced, it might feel like a light refresher. If you’re new, you’ll likely need to supplement it heavily.
My recommendation
To properly prepare for the exam, I recommend completing the following modules on Hack The Box Academy:
Active Directory Enumeration & Attacks
Windows Privilege Escalation
Linux Privilege Escalation
Login Brute Forcing
Using the Metasploit Framework
Network Enumeration with Nmap
Additionally, make sure you have a basic understanding of common web vulnerabilities like SQL injection, Remote Code Execution (RCE), and Cross Site Scripting (XSS), as these are useful for the CMS focused web section of the assessment.
The exam
The eCPPTv3 exam consists of 45 questions to be completed within 24 hours. It’s a hands on challenge where you connect to a lab environment and submit your answers directly through the portal.
While it’s framed as a practical pentest simulation, the reality is that most of the exam revolves around credential hunting, hash cracking, and brute forcing logins, especially on Windows machines. There’s very little real exploitation or vulnerability chaining involved. I encountered just one Active Directory technique, and it felt more like a side task than part of a real attack path.
The lab environment is stable, and the tools work as expected. There’s also no reporting requirement, which simplifies things but also removes a layer of realism.
In some cases, the difficulty comes not from technical depth but from intentionally obscure tasks—like searching for a password hidden in a random file buried deep in the file system, with no logical reason to look there. It doesn’t make the exam harder in a meaningful way, just more tedious.
If you’re comfortable with Hydra, hashcat, enumeration, and have the patience to dig through machines for clues, you’ll manage just fine. Just don’t expect a realistic red team workflow or advanced attack logic.
Also, let’s talk about this statement from INE’s own guidance: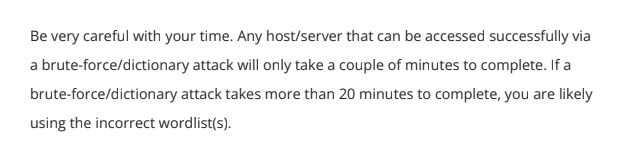
This statement is a lie. In reality, many brute force steps in the exam can take far longer, even with commonly used and solid wordlists. The exam often relies on guesswork and obscure file paths or usernames, not clean logic. If you follow this advice too closely, you’ll waste time assuming you’re doing something wrong, when in fact you’re on the right track—it’s just poorly designed.
To make things worse, INE recommends common lists like rockyou.txt and Metasploit defaults, but many valid credentials aren’t found there. In reality, shorter lists like xato-net-10-million-passwords-10000.txt, seasons.txt, and months.txt are more effective—yet they aren’t mentioned at all. This adds unnecessary confusion and makes the process more frustrating than it should be.
Would I Recommend It?
At this point, I recommend staying away from INE. Over time, they’ve clearly downgraded the quality of their certifications, and eCPPTv3 reflects that decline. The course lacks depth, the exam focuses more on brute force and guesswork than real exploitation, and the overall experience feels outdated and unstructured.
If you’re new to the field, eJPT is probably the only INE cert still worth taking—it’s beginner friendly, well paced, and a solid introduction to offensive security.
For anything beyond that, you’re better off going with alternatives like CPTS from Hack The Box, PJPT from TCM Security, or PT1 from TryHackMe. They offer better labs, more relevant content, and a more realistic approach to learning and testing offensive skills compared to what eCPPTv3 currently delivers.
TL;DR
If you’re new, go for eJPT. If you’re beyond that, you’ll get far more out of CPTS, PJPT, or PT1. INE just isn’t keeping up anymore.
